While email is a blessing for modern society it is not totally safe from cybercriminals. Among many security threads, email spoofing is a commonly seen malicious activity done by hackers. So, how do you keep yourself safe from them? In this blog, we are going to explain the anatomy of email spoofing and how you can be safe from it. Without further ado, let’s get started.

💡 Understanding Email Spoofing
So, you might be wondering, what is email spoofing? Well, it is a deceptive technique to disguise the origin of an email used by cybercriminals. In this way, hackers try to mislead people to various scams, phishing attacks, and malware distribution campaigns. While sending emails, they use a fake sender address that appears to be original. So, you need to be aware of email spoofing to save yourself from these cyberattacks.
🔎 Example Of Email Spoofing
Let’s have a look at the following image to understand email spoofing. It appears as if the email was sent from the website owner, but after closer examination, you will notice a slight difference in the domain name. At first look, it can be difficult to detect this difference and get misled.
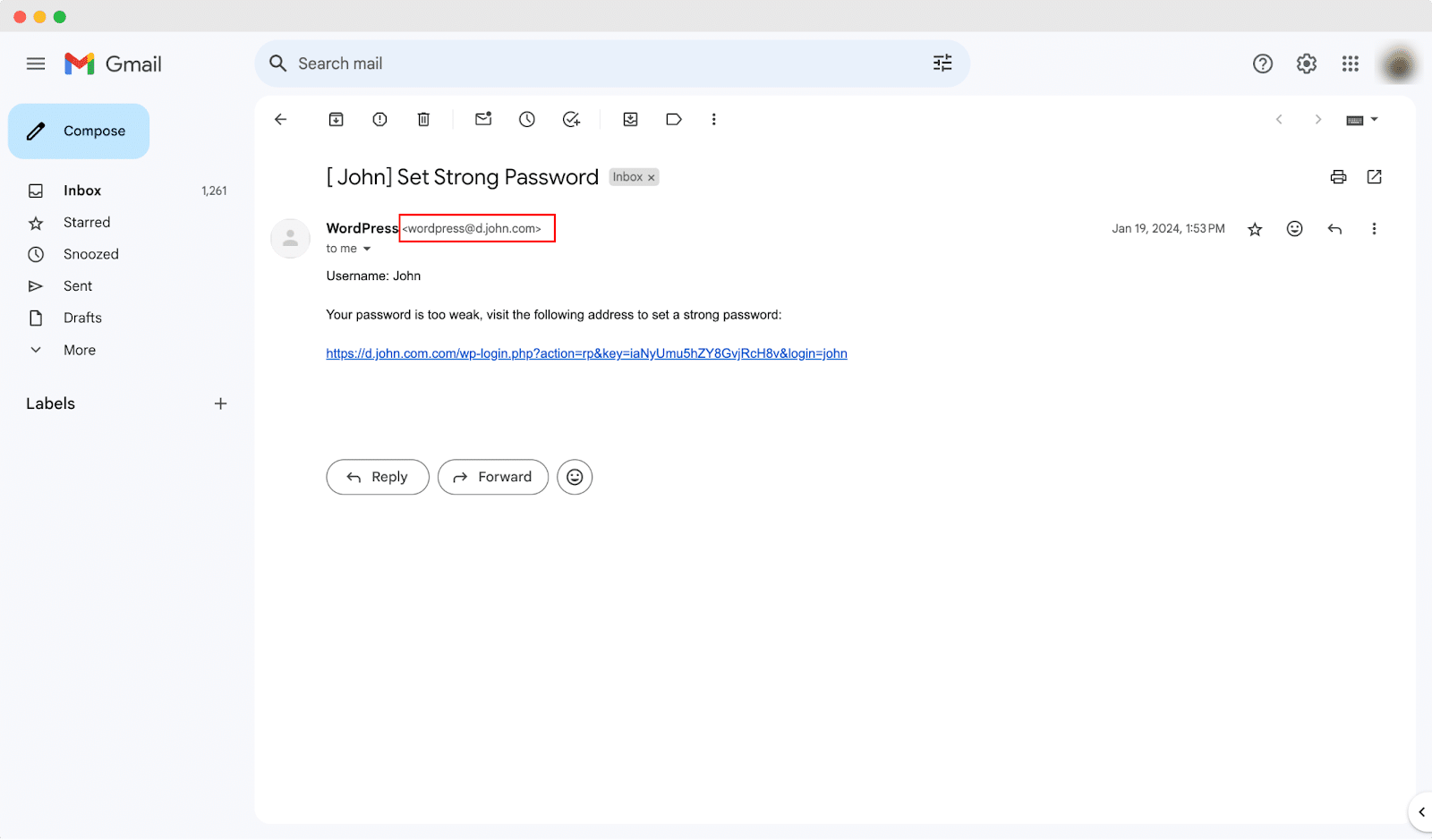
📖 Anatomy of Email Spoofing
Now that you have a basic understanding, let’s dive into the anatomy of email spoofing. In this section, you will learn how these malicious activities are designed by the attackers.
⭐ Sender Address Forgery
Email spoofing is fundamentally about manipulating sender addresses. Attackers frequently create emails with sender addresses that look like trustworthy sources. So, once it appears as a trusted source, people get very easily misled and the hackers take advantage of it.
⭐ Header Manipulation
Email headers contain metadata that tells you where the email came from and how it got there. By altering header information such as “From,” “Reply-To,” and “Received,” scammers can hide their identities and make it difficult to track the email back to its origin.
⭐ Phishing Tactics
Email spoofing is commonly used in phishing attacks, in which attackers simulate trusted entities to trick recipients into disclosing sensitive information or carrying out malicious actions. These emails frequently use social engineering strategies to create urgency or anxiety in recipients, causing them to act quickly without checking the email’s legitimacy.
⭐ Automated Spoofing Tools
With the rise of sophisticated spoofing tools and services, attackers may now set up large-scale email spoofing campaigns with ease. These applications automate the process of forging sender addresses and altering headers, which increases the effectiveness of spoofing attacks while avoiding detection.
📋 Email Spoofing Precautions
So, how can you protect yourself from email spoofing? To avoid being scammed, you may use some email spoofing prevention measures. Let’s look at the steps you can follow to stop email spoofing.
⭐ Email Authentication Protocols
As the attackers disguise their emails through various techniques, you can implement strong email authentication methods to prevent that. Technologies such as SPF, DKIM, and DMARC can help you to ensure the validity of incoming emails and detect spoofing attempts.
⭐ Use Email Filtering Solutions
Email filtering solutions can help you prevent email spoofing. You can use powerful email filtering and anti-spoofing systems to detect and prevent fake emails before they reach your inbox. These advanced filtering mechanisms analyze various aspects of incoming emails, such as sender information, content, and attachments, to identify potential spoofing attempts.
⭐ Regular Software Updates
While you can use different solutions to stop email spoofing, hackers are also constantly looking for loopholes. Therefore, you should always keep email servers, clients, and security software up-to-date with the latest patches and security enhancements to mitigate known vulnerabilities and protect yourself.
⭐ Watch for Unknown, Odd, or Spoofed Email Addresses
Always keep an eye open for the spoofed emails. Look out for any irregularities, oddities, or signs of email spoofing in the sender’s address. In this way, you can better protect yourself from falling victim to email spoofing attacks and avoid potential scams or security breaches.
⭐ Never Reply To Spoofed Email
Spoofed emails will not be a problem for you if you don’t reply to them. Once you have received an email in your inbox, examine the email address carefully. If you notice any suspicious activity or if the sender’s address seems unusual or unfamiliar, it’s best to mark the email as spam. This option could come in handy for you.
⭐ Do Not Open Unknown Attachments or Links

Another important precaution is to avoid opening attachments or clicking on links in emails from unknown or untrusted sources. These attachments or links could contain malware or lead to phishing websites designed to steal your personal information. Always verify the sender’s identity and exercise caution before interacting with email content, especially if it’s unexpected or seems suspicious.
⁉️ Frequently Asked Questions
Before ending this blog, we want to answer some common questions that you might have about email spoofing. Let’s have a quick glimpse at them.
How can I prevent spoofed emails from being sent using my email address?
To prevent spoofed emails, ensure your email account has robust security measures such as strong passwords, enabling two-factor authentication, and implementing email authentication protocols like SPF, DKIM, and DMARC.
What should I do if I receive a spoofed email that appears to be from my own email address?
If you receive a spoofed email from your own address, do not respond or click on any links. Instead, mark it as spam or phishing and delete it immediately.
How can I stop email spoofing on Gmail?
To prevent email spoofing on Gmail, enable the “Sender Policy Framework (SPF)” and “DomainKeys Identified Mail (DKIM)” authentication methods in your domain settings. Additionally, you can set up DMARC (Domain-based Message Authentication, Reporting, and Conformance) to monitor and protect your domain from spoofing.
How can I prevent email spoofing on Office 365?
To stop email spoofing on Office 365, configure Exchange Online Protection (EOP) to enforce SPF, DKIM, and DMARC policies. Additionally, educate users about recognizing and reporting suspicious emails.
How do I prevent email spoofing on Outlook?
To prevent email spoofing on Outlook, ensure your email domain has proper SPF, DKIM, and DMARC records configured. Outlook also offers features like message encryption and advanced threat protection to enhance security.
What is the difference between email spoofing and phishing?
Email spoofing is the process of faking the sender’s email address so that it appears to be from a legitimate source, whereas phishing is a broader term that refers to a variety of deceptive strategies used to trick recipients into disclosing sensitive information or taking unsafe actions.
What should I do if someone is sending emails under my name?
If someone is sending emails under your name, immediately notify your email provider, update your account security settings, and consider implementing email authentication protocols like SPF, DKIM, and DMARC to prevent further abuse.
🛟 Avoid Becoming a Victim Of Email Spoofing
Understanding the anatomy of email spoofing and applying proactive security measures will help you avoid becoming a victim of it. So, as the cybersecurity landscape evolves, remain watchful, and secure to stop these attacks.
আপনি এই ব্লগ দরকারী খুঁজে পেয়েছেন? যদি আপনি করেন, তাহলে দয়া করে আমাদের ব্লগে সাবস্ক্রাইব করুন এবং আমাদের সাথে যোগ দিন ফেসবুক সম্প্রদায় for regular updates.









